RDP? VPN?… I Just Want to Work!
As the IT landscape continues to change we make changes to security settings that are always intended to help, but sometimes the result is a bad user experience- most specifically remote connections. Some of you may have asked yourself lately, “Why do I have to open two programs now when I want to remote into my office?” Indeed that is a very good question. The short answer is simple, security. A VPN connection is more secure than an RDP connection by itself.
Two acronyms in the same sentence? That is how you know you are reading an IT blog.
So why the recent changes? There is a rising trend in ransomware specifically attacking RDP connections. For those of you with the good fortune to not be familiar with ransomware, it’s a new generation of infection that uses unbreakable encryption to hold your data hostage. At the time of this writing, Mecklenburg County’s data is currently being held hostage for a $23,000 ransom. As a result, inmates are being processed by hand and most departments have had to switch to paper records while data is restored from backups. The county expects the process to take weeks.
So what is RDP?
RDP stands for Remote Desktop Protocol. A proprietary protocol developed by Microsoft that’s been in circulation since the first release of Windows XP. It provides a graphical interface to a remote computer or server.
You may be familiar with the name Terminal Services. The two are synonymous. It is typically the fastest and most convenient method for remote work.
Is RDP insecure?
Not inherently. The problem arises when trying to use RDP to access a workstation or server from outside the office (which as we know is very easy to do). To allow outside connections, a port must be opened in the firewall. Savvy hackers are using tools like Shodan to scan the internet looking for these open ports. Think of it as leaving a window in your house unlocked in case you lose the key to your front door. If someone comes along and tries them all, they’re going to find that one unsecured window. This analogy doesn’t quite hold up because the accounts that can log in to the server are password protected, but it does allow someone to use a password attack on your system.
What is a VPN?
VPN stands for Virtual Private Network. Think of it as a network extender. A user can be anywhere in the world, but if they are connected to their VPN they will have access to network resources as if they were sitting in the building. A virtual private network creates a secure tunnel between the user and their destination. All the data that passes between is encrypted. Equally as important, the VPN connection makes it possible to keep all external ports on a firewall closed.
Does VPN replace RDP?
Unfortunately, it can’t. A VPN connection can only make an RDP connection more secure. The two technologies work in tandem. The VPN creates a rock-solid secure connection to the corporate network; the previously mentioned tunnel, and RDP allows access to a user’s desktop or terminal server. Without a VPN connection, a port must be opened in the firewall to allow the RDP traffic through.
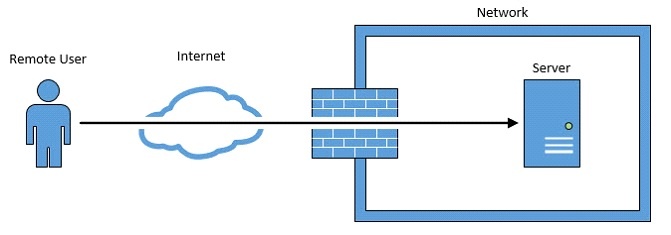
Fig.1 A user connecting directly to a server using RDP. Concessions must be made to the security of the firewall to allow this.
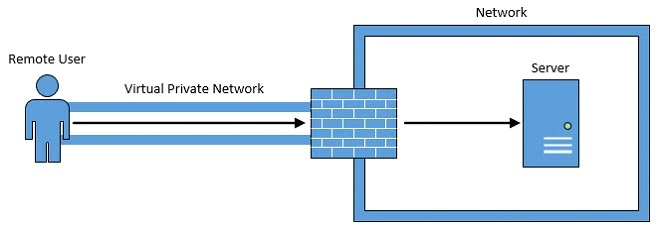
Fig.2 A user connecting to a server via RDP while being protected by a VPN connection.
In Summary:
This type of attack targets small and medium businesses (Mecklenburg County not withstanding). Larger companies almost always have sophisticated security infrastructure and on-staff IT personnel that specialize in security. In a study conducted by Sophos Labs, the largest company to fall victim to this type of attack had 120 employees. The average was 30.
No single security mechanism is enough to thwart infections anymore. IRIS uses a security strategy referred to as “defense-in-depth” to help ensure the integrity of our client’s network. Multiple safeguards are put in place to prevent bad guys from getting onto your network. If they manage to find and get past the firewall, multiple safeguards are in place to prevent them from gaining access to the server(s). And if they manage to gain access to a server, multiple safeguards are in place to prevent them from executing malicious code. A VPN is just one item in the security toolbox we provide to our clients.
If you’re curious how IRIS can help secure your network, or if you are a current client and would like more information on any of the safeguards in use on your network, just give us a call. We love to talk about this stuff.


