Vulnerability Assessment for the Healthcare Industry
On September 30th The White House designated October as Cybersecurity Awareness Month and encouraged the public and private sectors to take immediate action to protect against cyber threats:
“Cyberattacks affect our day-to-day lives, our economy, and our national security. By destroying, corrupting, or stealing information from our computer systems and networks, they can impact electric grids and fuel pipelines, hospitals and police departments, businesses and schools, and many other critical services that Americans trust and rely on every day”.
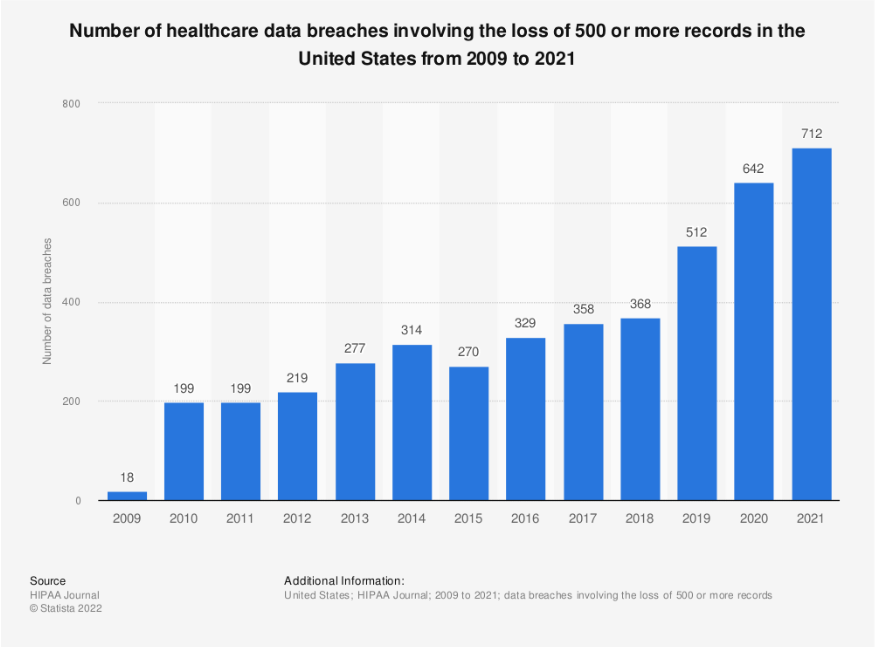
Since the start of the Covid-19 pandemic in 2020, the healthcare industry has been one of the largest attack vectors in United States. According to data published from Statista.com in January of 2022, healthcare organizations in the Unites States saw the highest number of large-scale data breaches (resulting in the loss of over 500 records) to date in 2021. The number of such cases has increased in recent years, going from 18 cases in 2009 to 712 cases in 2021, up from 642 data breaches in the year prior.
Electronic Protected Health Care information (ePHI) is the primary asset that attackers are seeking out and stealing.
Prior to the Presidential proclamation on September 30th, the Healthcare Cybersecurity Act of 2022 was introduced as a bill to the Senate on March 23rd 2022. This bill requires the Cybersecurity and Infrastructure Security Agency (CISA) to undertake activities to improve the cybersecurity of the health care and public health sector. Additionally, on January 5, 2021, the HIPAA Safe Harbor Bill was signed into law. The purpose of the bill was to encourage healthcare organizations to adopt recognized cybersecurity practices to improve their defenses against cyber-attacks.
Organizations that have adopted recognized cybersecurity best practices and have completed a HIPAA Security Risk Analysis, reduced identified risks to a low and acceptable level, and have implemented technical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information (ePHI) will be treated more leniently by the Office of Civil Rights (OCR) if a breach should occur.
IRIS Solutions can help your healthcare organization comply with the HIPAA Security Rule and help protect your assets from theft. Our security professionals can help assess risk within your environment, test the controls you have in place to keep them safe and look for vulnerabilities in your network that could be exploited by cyber criminals that could lead to a breach of ePHI.
Vulnerability assessment is an excellent start to get in compliance with or maintaining compliance with the HIPAA Security Act HIPAA §164.308(a)(1)(ii) (A).
Conducting a vulnerability assessment is important because the exercise will identify security flaws that exist in your information technology environment before they are discovered by a malicious hacker. Once the vulnerabilities are discovered you can correct them and lower your risk of becoming a victim of success cybersecurity attack.
A vulnerability assessment will discover common security weaknesses such as:
- Operating systems and applications that are not current with the latest security updates or patches.
- Unsecure legacy operating systems that are no longer supported by manufacturer.
- Open ports on perimeter defenses and other devices that allow malicious attackers to easily gain access to your private computer network.
- All Common Vulnerabilities and Exposures (CVE) that exist on the computer network.
Common Vulnerabilities and Exposures (CVE) is a database of publicly disclosed information security issues. There are currently over 163 thousand CVE records catalogued and made publicly available by the CVE program. You can explore the database at www.cve.org. Why does this matter? Because it is important to recognize that new information security flaws are discovered regularly and then shared publicly. Sharing the information is not restrictive. Everyone can search the CVE database, including the hackers that intend to attack your computer network.
Executing routine vulnerability assessments will discover all the known vulnerabilities on your network before the bad actors have an opportunity to exploit them. Vulnerability assessments are nonintrusive and not disruptive. Typically, a vulnerability assessment can be completed in a day or two. The results of a vulnerability assessment are documented and provided to the stakeholder complete with recommendations around remediating any weaknesses found.
It is important to conduct vulnerability assessments regularly, at least every quarter if not more frequently. This is due to the dynamic nature of information technology. Many changes occur on a day-to-day basis that can introduce new exposures associated with information security. Examples include:
- The introduction or removal of employees and business process.
- The implementation or elimination of hardware, software, or business applications.
- Configuration changes made to any element of the technology environment.
- Newly discovered bugs and flaws found in off the shelf commercial software products.
Security shortcomings found during a vulnerability assessment can almost always be fixed. Many times, the fixes are very easy to accomplish. Roughly 60% of all reported cybersecurity breaches occurred because the bad actors exploited common vulnerabilities and exposures (CVE). This means that roughly 60% of all reported cybersecurity breaches could have been prevented if the victim had simply conducted a vulnerability assessment and made small improvements to their cybersecurity posture that would have eliminated a substantial amount of risk.
If you would like to discuss vulnerability assessments in greater detail, please reach out to success@irissol.com or ask about it during your next technical business review with the customer success team.


